In Today’s Era of technology, connectivity is increasing day by day, and to maintain the interconnections between them companies must have a powerful backend to handle these workloads
A Denial of Service (DoS) attack is a type of cyber attack in which a perpetrator seeks to make a particular computer or network resource unavailable to its intended users by overwhelming it with a flood of traffic or requests. The goal of a DoS attack is to prevent legitimate users from accessing the targeted resource.
In Distributed Denial of Service (DDoS) attack, an attacker uses multiple IPs or systems or a network of botnets to achieve the Downtime on a target site in less amount of time, DDoS attacks are much more powerful than DoS Attacks, As a result, it gets worse to get back the service online if DDoS attack is continuously running on it
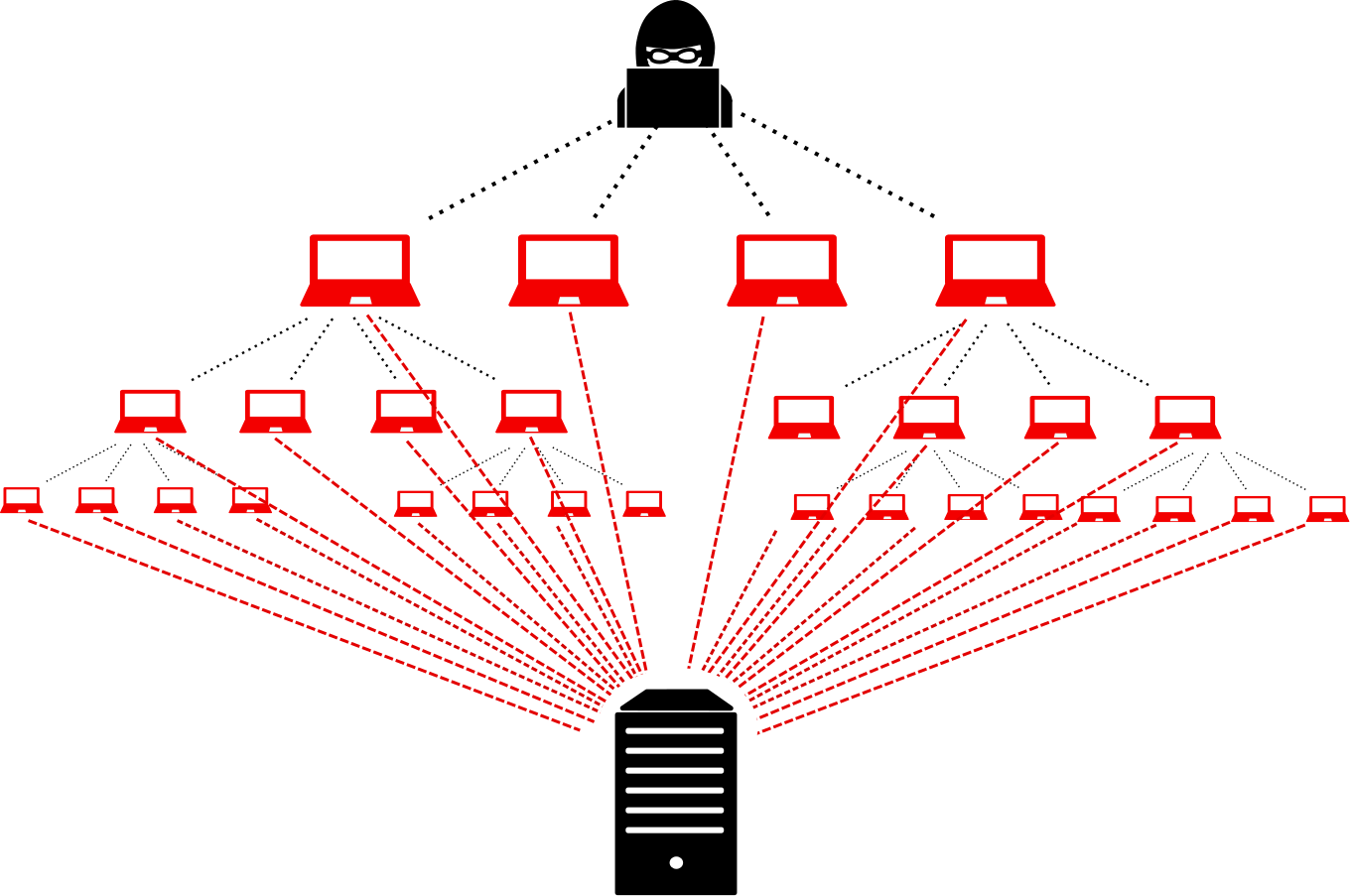
DoS/DDoS Attack Can be classified into four categories:
• Ping of Death (PoD)
A Ping of Death (PoD) attack is a type of denial-of-service attack that involves sending a malformed or oversized ICMP (Internet Control Message Protocol) echo request packet, also known as a “ping,” to a targeted computer or network. The goal of the attack is to cause the targeted system to crash or become otherwise unavailable. The attack exploits a buffer overflow vulnerability in specific operating systems, which can cause the system to crash or reboot when it tries to process the oversized packet. The attack can be launched from a single computer or multiple computers, known as a distributed denial-of-service (DDoS) attack. It was a standard attack method in the late 1990s but is now less common due to the implementation of security measures such as firewalls, intrusion detection systems, and patches for vulnerable operating systems
• Smurf
A Smurf attack is a type of DDoS attack that floods a targeted network or computer with a large number of ICMP echo request (ping) packets, using a network of infected computers known as a botnet. The attacker sends a large number of ICMP echo request packets to the broadcast address of a network, with the source IP address set to the IP address of the targeted victim, causing all devices on the network to respond to the victim, overwhelming their network connection and making the targeted system unavailable. This type of attack is less common now due to security measures, but it’s still important to be aware of the potential threat and take steps to protect yourself and your network.
• BufferOverflow
A buffer overflow DDoS attack is a type of DDoS attack that exploits a buffer overflow vulnerability by sending a large amount of specially crafted data to a targeted system, causing it to crash or become unavailable. This type of attack can be used to execute malicious code or cause a system crash. It’s an advanced type of DDoS attack that can cause serious damage to systems or networks.
• TearDrop
A Teardrop attack is a type of denial-of-service (DoS) attack that targets a computer or network by taking advantage of a vulnerability in the way that certain operating systems handle fragmented IP packets.
The attack sends a large number of IP packets with the “more fragments” (MF) flag set and with overlapping, but non-contiguous, fragment offsets. This causes the target system to crash or reboot because it cannot reassemble the packets properly.
This type of attack was more common in the past, but it is less common now due to security measures such as firewalls, intrusion detection systems, and patches for vulnerable operating systems. It’s important to keep systems and networks updated with the latest security patches to protect against known vulnerabilities like this one.
How to Mitigate DoS/DDoS Attacks:

There are several ways to mitigate DDoS (Distributed Denial of Service) attacks:
- Traffic filtering and rate limiting: This involves using firewalls, routers, and other network devices to filter incoming traffic and limit the rate of incoming traffic to a manageable level.
- Traffic shaping: This involves prioritizing legitimate traffic over attack traffic by using techniques such as Quality of Service (QoS) and traffic engineering.
- Content Delivery Networks (CDNs): CDNs can absorb and distribute attack traffic across a network of servers, reducing the impact on the targeted website.
- Scrubbing centers: Scrubbing centers are specialized DDoS mitigation services that can detect and filter out malicious traffic before it reaches the targeted website or network.
- Cloud-based DDoS protection: Cloud-based DDoS protection services, such as Amazon Web Services (AWS) Shield or Azure DDoS Protection, can detect and mitigate DDoS attacks in real time.
- Network and server hardening: This involves implementing best practices for network and server security, such as using secure protocols, keeping software up to date, and applying security patches.
It’s important to have a DDoS mitigation plan in place before an attack occurs and to continuously monitor the network for signs of an attack and respond quickly.
Conclusion:
if you are running a business in digital mode, customers must want high availability of services which creates a major impact on sales. so you must set up mitigation to have the capability for preventing these attacks.
Found it helpful, leave a comment for more content that you want to be next. 😊

2 Comments
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article. https://accounts.binance.com/en/register?ref=YY80CKRN